
Cyber Attack on Philabundance — Account Takeover (ATO)
March 16, 2024
What is Malware? Definition, Types, Examples, Prevention
April 28, 2024Email Attack Countermeasures Revealed in Google Cloud’s M-Trends 2025 Report

1. Key Take-aways from Google Cloud M-Trends
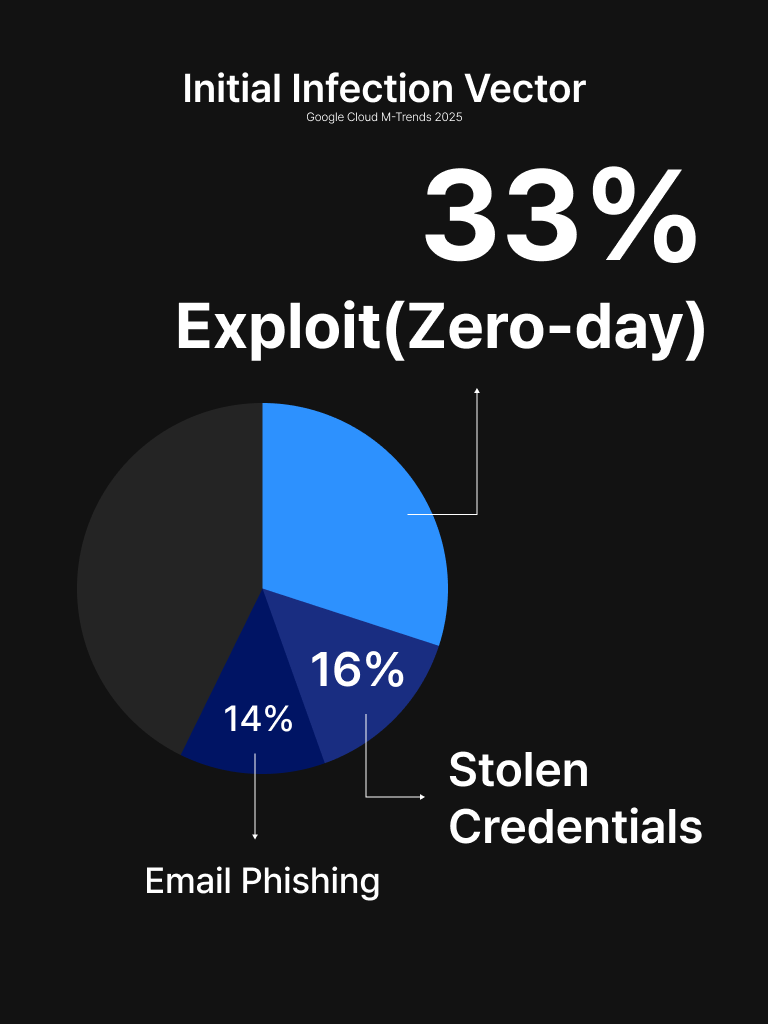
In 2024 the most prominent initial infection vector was zero-day vulnerability exploitation, followed by credential theft and email phishing.
After penetrating a vulnerability, attackers implant malware to obtain account information and then access mail servers to steal credentials, emails, and data. Because zero-day exploits are difficult to detect and respond to, a proactive strategy that anticipates unknown threats is essential.

2. Primary Counter-measures Against Cyber Threats
Countering Zero-Day Malware Attacks
ITU-T X.1236 (7.1.1) defines zero-day malware attacks as exploits launched before a patch is available.
For email-borne zero-day attacks, malicious attachments or links are inserted to trick users into clicking undetected.
ITU-T X.1236 (8.1.1, 9.1.1) recommends behavioral analysis (sandbox OS-change tests) that observes actions before permitting execution, detects harmful behavior, and isolates suspicious emails so they cannot be re-sent.
Countering Social-Engineering Attacks
Social engineering attacks manipulate psychological or social factors to trick individuals into divulging confidential information.
ITU-T X.1236 classifies four email-based techniques:
Forged Header (ITU-T X.1236 7.2.1, 8.2.1, 9.2.1)
A forged-header attack occurs when an adversary falsifies account information in the email header to evade detection, for example, spoofing the sender address of a well-known company’s help desk.
Countermeasure for Forged Header Block the message or warn the user whenever the Reply-To address differs from the apparent sender. Verify that the message passes SPF, DKIM, and other mail-transfer protocols, and monitor IP- and domain-reputation data to spot spoofed mail.
Look-alike Domain (ITU-T X.1236 7.2.2, 8.2.2, 9.2.2)
A look-alike-domain attack sends malicious email from an address that mimics a trusted sender’s domain.
Countermeasure for Look-alike Domain Calculate domain similarity against the recipient’s historical email records. If a sender’s domain is flagged as visually or textually similar, alert the user or quarantine the message. Criteria include character-count differences and altered top-level domains (TLDs). Security admins must also be able to add suspicious domains manually.
Account Take-over (ITU-T X.1236 7.2.3, 8.2.3, 9.2.3)
An account take over (ATO) attack steals a legitimate user’s mailbox credentials, then scans email history, requests wire-transfer changes, or exfiltrates confidential data.
Countermeasure for Account Take-over Profile each sender and detect changes in their location. Warn or block when the IP address, network route, or physical origin of an incoming email diverges from prior messages.
URL Phishing (ITU-T X.1236 7.2.4, 8.2.4, 9.2.4)
URL-phishing attacks lure users to websites that solicit credentials or other sensitive data, all while masquerading as messages from trusted organizations.
Countermeasure for URL Phishing Trace every URL in the email body to its final destination and flag pages that request personal information. Pay particular attention to input fields asking for usernames and passwords.
3. References
ITU-T X.1236 (Security requirements and countermeasures for targeted email attacks)
https://www.itu.int/ITU-T/recommendations/rec.aspx?rec=15710&lang=en
Google Mandiant M-Trends 2025


