
What is Zero-Day? Definition, Risks, Examples, Prevention
1월 14, 2024
What is DDoS? Definition, Types, Prevention
2월 2, 2024Public Sector in Toronto, Canada Faces Cybersecurity Crisis Amid Surge in Ransomware Attacks

1. Summary
2. Overview
According to Deloitte, 91 % of all cyber attacks begin with spear phishing emails. Despite years of user awareness programs, attackers continuously evolve their tactics.
A recent study by the European Union Agency for Cybersecurity (ENISA) highlights growing vulnerabilities in public administration and education. These entities hold vast troves of sensitive citizen data and operate critical infrastructure, making them high-value targets. Service interruptions triggered by phishing emails can create confusion and urgency, raising the likelihood that victims will pay a ransom. This article therefore explores technical solutions that let organizations stay ahead of sophisticated threats.
3. Attack Case Analysis - Attack Type
Case: Ransomware attack on the Toronto Public Library (TPL) caused by Black Basta – Malware in an attachment, Malware in uniform resource locator
On Sunday, 29 October 2023, the TPL branch manager received an urgent call: the library’s computer systems were inaccessible. The main site tpl.ca was offline, and public PCs, printing, and “Your Account” services were down.
While TPL initially withheld details, ‘BleepingComputer’ later confirmed via a ransom note photo that the Black Basta gang was responsible.
Black Basta typically gains network access through phishing emails, malicious ZIP files downloaded from spoofed URLs, and infected attachments. Once a user opens the file, the malware disables antivirus, locates data repositories (including mirrored backups), encrypts them, and then demands cryptocurrency or threatens to leak the stolen data publicly.
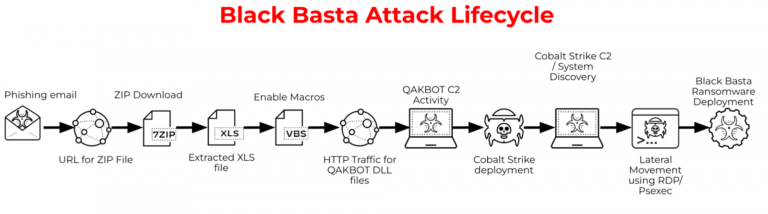
This type of attack is outlined in the international standards sections [7.1 Malware email attacks]. Attacks using malicious code can be divided into two types: phishing mail that leads to secondary and higher destinations through URLs, and inserting malicious codes into the URL in the attached file.
In the realm of email security standards, these types fall under the category of [7.1.2 Malware in an attachment] and [7.1.3 Malware in uniform resource locator]. These standards carry international credibility, being registered with the International Telecommunication Union (ITU), a specialized agency of the UN.
7.1.2 Malware in an attachment
A malicious attachment is one type of threat in which attackers conceal malware inside commonly emailed files. The attachments within these malicious emails can be disguised as documents, executable files or even image and video files. These files can also be encrypted with other extensions. Attacks using executable files may involve spoofing the sender’s address to deceive the recipient into opening emails with malicious documents.
7.1.3 Malware in uniform resource locator
A malicious URL attack is made by inserting a clickable link containing malware in emails to induce users to visit malicious websites. Also, malicious URLs can be contained in a large attachment or the body of an email. This can be an attack that causes malware to be executed when a user clicks on a URL in an email or regular attachment, not only at the time of delivery.
4. Attack Case Analysis - Solution
To protect valuable information assets from these types of malicious attachments and URLs, Compliance with the requirements and countermeasures specified in the international standards is important.
Compliance with Clauses 8.1 [Security requirements to counter malware email attacks] and 9.1 [Counter-measures for targeted email attacks] in ITU-T X.1236 provides concrete safeguards.
To counter malware in an attachment attacks, the following requirements must be met:
- It is recommended to detect a forged file extension in various file formats.
By implementing this security requirement, proactive measures against malware in an attachment attacks can be taken as follows:
- Big data-based inspection scans all inbound and outbound email data of users on a regular basis via cloud service to extract malicious attachments that require further inspection. It determines whether there is a risk of targeted email attacks based on the data stored in the big data system. This feature identifies and detects a forged file extension.
To respond to malware in uniform resource locator attacks, the following security requirements must be met:
- It is required to trace the final destination of URLs within multiple linked URLs while checking all URLs for malware.
By implementing this security requirement, proactive measures against malware in uniform resource locator can be taken as follows:
- URL image conversion disables opening a URL link in a perceived dangerous environment where the attached malicious URL is recognized.
Complying with these proactive measures can effectively reduce the risk of targeted email attacks with those types of attacks above. Moreover, to understand and respond to these attacks, it is necessary to be aware of and adhere to international email security standards, using solutions that follow them. Mail Inspector Platform provides solutions that align with these necessary functional requirements.
5. Conclusion
6. Reference
91% of all cyber attacks begin with a phishing email to an unexpected victim
SPACING INVESTIGATION: TORONTO PUBLIC LIBRARY RANSOMWARE ATTACK, PT. I
Toronto public library outages by black basta ransomware attack
Toronto Public Library confirms data stolen in ransomware attack
Threat Assessment: Black Basta Ransomware
https://unit42.paloaltonetworks.com/threat-assessment-black-basta-ransomware/


